Let’s talk a little bit about what are the strategies for risk management and how can a virtual CISO help you with your risk management strategies. We already made some other videos about what to expect from a virtual CISO cybersecurity assessment. Most risk findings are going come out of an assessment.
When we talk about risk management strategies, we already know what the risks are. Some process, some assessment has already happened in which we’ve identified what the cybersecurity risks are for your company. So the next stage is;
- What do we do with these risks?
- How do we manage these risks?
- How do we prioritize these risks?
That’s what the risk management program sets to answer.
So, with that context, I want to show you a little bit about the risk mitigation strategies that we use at Asher Security to help our clients decide which risks to take on first and how to take them on. Let me just show you, here’s a report, a synonymized report that we prepared as a result of our rapid risk assessment. Notice the first thing I want to point to is the risk ranking.
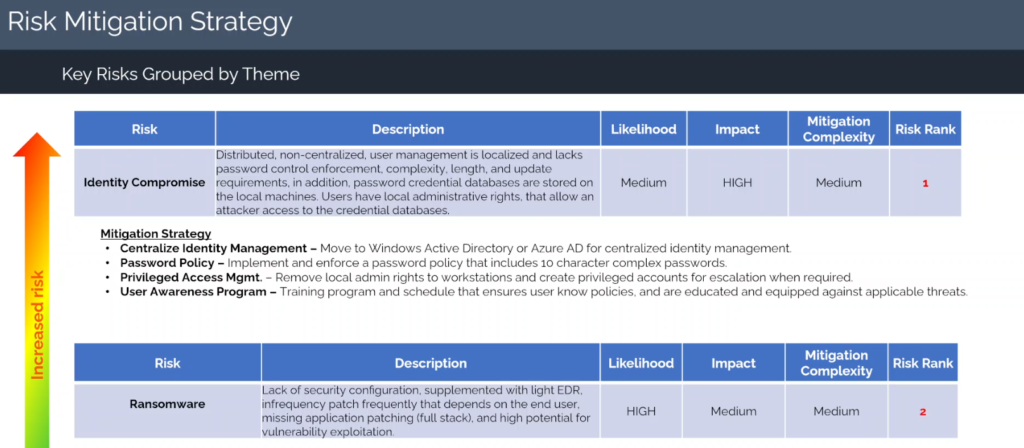
Right here, risk rank. We attempt to rank all of the risks based on priorities. So, the first step in your risk management strategy should be to prioritize your risks.
A virtual CISO can help you prioritize your risks. They can propose what we think. Ultimately, at the end of the day, the stakeholder of the business always has the right to rearrange these.
Business stakeholders are always going to have more business context than what we will have from being in there from four to six weeks doing an assessment. They’re going to have much more clarity. There could be things that got missed.
There could be people that were not questioned. There could be crown jewels that were overlooked. But this, hopefully, has a high fidelity and integrity of what the risks are.
And your CISO or your virtual CISO has attempted to rank these. And that’s what we do here in this upper right. We’re going to start with the highest risk, and we’re going to talk about what the risk is.
This risk in particular is around identity compromise. You’re going to write some kind of description. What does that mean? Because that doesn’t mean anything.
I mean, one of the goals of a virtual CISO is brevity, is to communicate in a simple, brief way. The description is what’s going to add a little bit more context of why is that a risk? In this situation, we had distributed, non-centralized user management. It was localized to endpoints.
There was no password control enforcement. There were no complexity requirements, including length or updates. In addition, password credential databases are stored on local machines, and users have local admin rights that could allow an attacker to capture that credential database.
So let’s just walk through this real quick. If a local user has admin rights to their endpoint, the user is essentially the number one firewall. So, threat, the user is responsible for filtering threats to their endpoint.
If the user is not trained on what those threats are, and there’s no user awareness program, or there’s no attestation about them being trained, or that they understand, or if there’s no mechanism for them to escalate concern or report things like alerts, that user is at high risk. And if they click on a link, or open an attachment, or visit a website, or stick a USB drive in, or something that can introduce an exploit to their machine, there is a high potential that the risk can then pivot and capture that database where credentials are stored, and take it out. And then the attackers try to crack that database, reverse engineer what those credentials are.
In a system where they’re using local passwords, and you’re able to grab the local admin password, there’s usually one that you can use to pivot to all the other machines. So that’s all I’m saying. There was, so let’s, there’s your description.
Let me get off my horse about how big of a deal that is. Okay, so within your risk mitigation strategy, you titled the risk, we have a description that kind of fleshes it out a little bit more about why, and then we’ve got a likelihood and an impact. And this is just good risk management practice.
You’re going to see this not only in cybersecurity risk management, but in all types of risk management disciplines, you should have that. The likelihood of this was a medium, the impact would be high. And then the next box we have here is mitigation complexity. And this is really some kind of indicator of like how hard would it be for us to fix this. How hard would it be to get rid of this risk? In this situation, it’s a medium.
Now here’s where the rest of the second half of the risk mitigation strategy comes in, right here, mitigation strategy. And in this example, we have four bullet points, four recommendations that can be implemented to either remove or reduce this risk, get it off number one, that’s the goal. We can centralize identity management, we can implement some type of password policy, we can implement privileged user access, and finally, we can implement some level of user awareness program.
So some training, right? So that’s what a really good risk mitigation strategy looks like, and that’s how a virtual CCO can implement a risk management strategy for you. And then just keep walking these down, one, two, three, four.
All right, there we go. We listed about 10. We listed about 10 risks, that’s pretty normal.
You want to be between five and 10. Anything after 10, definitely list them. But the effort that goes into taking a risk and fleshing it out to this detail, actually ranking it and comparing it to others, and thinking about that strategy and how to reduce that actually takes a lot of time and a lot of resources.
You just want to get those top 10 because in hindsight, there’s been times where we’ve worked really hard to flesh out and recommend risk strategies, mitigation strategies for a lot of them. But the truth is that it’s really hard to get traction. You’re probably not going to see a company actually remediate that many risks in a short timeframe.
I would say do these top 10, and then once you’re done, let’s go back and validate that they’ve been done, and then we can remove them off what we call our risk register, and then we’ll raise the other ones up, and then we’ll review those and take the time to put mitigation strategies in. I hope that makes sense. The other thing that I could show you here, let me flip this, I’m going to show you something else.
From a risk management or a risk management strategy, mitigation strategy, what I just talked about was a risk register. A risk register is a document in which you are documenting every risk you find. And there should at least be 10 risks in here.
More than likely, there should be around 40 to 100. So don’t worry about a risk being too small. Your job is risk visibility, and the risk register is the documented risk visibility tool or mechanism to be able to do that.
We have the documented risks. We have the impact description, impact and probability, impact and likelihood. Those are the two things that you see a lot.
And then just kind of like our other sheet where we did risk priority, here we have a priority level also. And this for us, we are using a risk register tool that we adopted. We did not develop this.
I wish I could give credit, but I can’t cite the source right now. But this is a field that basically just does an equation of multiplication between the impact level and the probability level. And just so you understand what I’m saying, this example here has an impact level of five.
It has a probability level of five. That’s the highest it can go. So, it does five multiplied by five with the probability level or a priority level, excuse me, of 25.
That’s the highest. You’re going to have to kind of shoot the wind on these. And I don’t mean to be unprofessional, but I do want to be transparent enough to say, these are best guesses based on your experience and training.
That’s the best we can do. If someone disagrees with them, we can change them. That’s not a problem.
But you’re putting these numbers in to try to come up with this. So then you take your priority level and you build a risk matrix. And that’s what you see over here.
A risk matrix is the number one tool to communicate your risk posture with executives on a consistent basis. And there’s a couple keywords there. The number one keyword is consistency.
You really want to be consistent. The number one thing that I see executive leaders get upset with is when you bring a different approach to reporting risk to them every time. They are trying to learn, they’re trying to adapt, so they want consistency.
Second thing is simplicity. And when we use this risk matrix, it’s really nice because there’s two very simple communication attributes to this that I’m sure that you’re already seeing. Number one is color, and number two is number.
Numbers are a great way to bridge the gap between a nerdy cybersecurity geek and an executive business leader. They allow us to speak a common language, kind of like, I don’t know, I probably shouldn’t even do this, but I think there’s been some alien movies in which aliens come and visit Earth and we use math to communicate with them. I think that is the perfect example of a cybersecurity nerd trying to communicate with business executives, and numbers are a great way to do that.
This number here isn’t your score, it’s how many findings are in the very likely row in the critical column. This is how many findings you have in this area. So you would say to your executives, we have 20 critical risks right now.
And then the orange here, these aren’t combined, but you have 15 and 10. So you also have 25 high risks, and five medium and two low. And then they say, well, what are these? And then you can pivot back to your risk register, maybe filter or just give maybe a slide.
If you are presenting to executives, you should really anticipate what questions they’re going to ask you. And I’m telling you right now, they’re always going to ask, what are these? You don’t need to go into detail, you just need to show it to them. They want to know that you know what they are, and they want to know what your proposal to do something about them is.
So even though they are going to propose the risk appetite, it’s up to them ultimately to dial in how much we remediate and what we just leave. I can tell you they’re always going to be concerned about this so be prepared to have a brief, either a slide or pivot to your risk register and filter out what those things are and be ready to make a statement about how you propose to handle those and ask them for the right resources if you haven’t already to handle those. I hope that answers your question on virtual CISO risk management strategies.
Those are a couple risk management strategies that I have. Number one, identify the risks, prioritize them, pick the top 10 and list out what the mitigation strategies are. Leverage a risk register,
And then finally communicate that in a consistent way using a risk matrix. If you do that, oh, your life is going to be so much easier. The secret in all this, I’m going to tell you this right now so you don’t get heartburn over it.
The hardest thing is identifying risks. So it’s really hard to have a mind that’s always thinking about what the risk factors are. We are coming out with some tools.
A matter of fact, I’m actually trying to come out with a series of videos that goes over about 50 different risks. We want to equip you on ways to go, “hey, is this a risk and line it up with that business and you’d be able to populate your risk register.”
Let me know what questions you have. Keep securing and stay joyful, right on.

Recent Comments