If you were given a budget of one million dollars for your security program how would you use it? How do you even go about answering that question?

I once visited a company that had rooms full of security equipment and technology. They were looking to hire people. When I asked what key fields and talents they were looking for, they said they weren’t sure, but it would be nice if the employee candidate could install the stuff that was stacked and sitting inside boxes.
They had a lot of ‘technology‘ but no ‘people‘ or ‘process‘.
I knew a guy that was amazingly talented with risk and information security. I wanted to be mentored by him. He had the mental ability to map and articulate all the security concerns, mitigating controls, compensating controls, remediation steps, and knew what residual risk had to be transferred or accepted. I’m pretty sure he could read the matrix. The problem was he didn’t have any budget. He couldn’t buy anything.
The company employing him had a lot of ‘people’ (skills) but no ‘technology’.
A successful security program is a strategic balance of three critical fields:
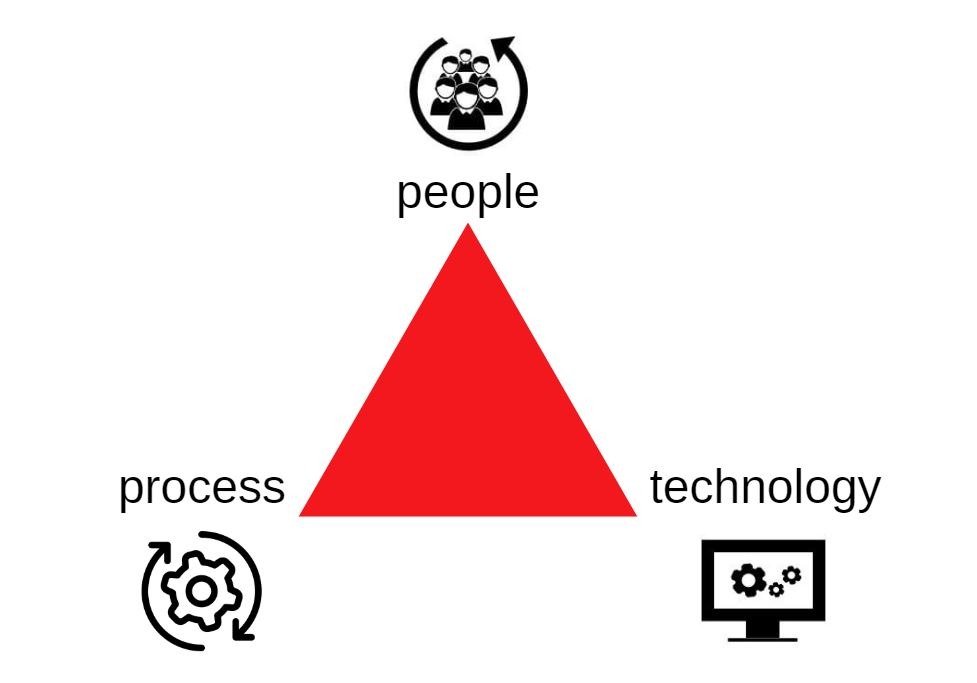
In the two examples I shared above (both true), you can find situations of security programs that have too much of one and not enough of another.
A security program with unbalanced resources will greatly limit the ability your program has to reduce risk over time.
Frameworks
I’m guilty of this, focusing on the security program framework and not what supports that framework.
In an article, I’m working on called ‘7 Layers of a Successful Security Program’ I define key areas of a program that are sequential building blocks. They can be used to build a program that reduces risk. My attempt was to refocus. I often write to clarify things to myself, not my readers (sorry if that is offensive to anyone). Someone once told me ‘writing is thinking‘. And another quote is, ‘teaching is leading‘. Explaining things forces us to articulate thoughts and finish the mind mapping process. All that said, my point is that my goal in writing the ‘7 Layer’ article was to go back to the basics and attempt to draw and plan a program that starts with the basics, and doesn’t get hung up in the media and new-fangled tech and lingo. I find I’m always going back to the basics in life.
Using this article to help clarify my point, let’s look at the first four of those seven steps:
- Asset Management
- Hardening & Compliance Standards
- Vulnerability Management
- Security Logging & Alerting
Those are all great things, but if we examine each one further what we actually find is they are a unique combination of people (skills), process, and technology. You cannot successfully implement any of those practices without those underlying resources.
Resource Pillars
People, process and technolgoy are the pillars that the rest of the program rests on. I won’t go as far as saying they are the ‘foundation‘. I would say that the business itself is the foundation, as without the business there wouldn’t be a security program. On top of that is the culture, leadership, philosophy, and vision that supports these pillars. But for ease of conversation, let’s pick up as the pillar level.
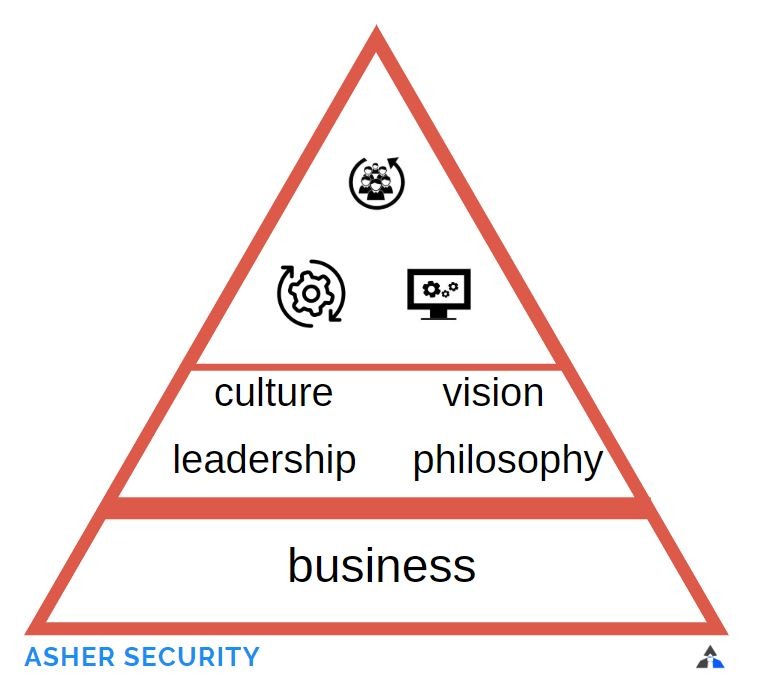
People: People have skills. They can develop skills. People use skills to do amazing things. Just as a builder uses his ‘framing’ skills to build the bones of a new house, security people with skills about the OWASP top twenty have the ability to think through risks of application exploits impacting production systems.

Side note: I once knew a guy that had the skill of knowing the value of PIE. He carried around a three-ring binder so that when you asked him what the one hundredth and twenty-third number of PIE was he could hand you the notebook to verify his verbal answer. It was amazing. I’m not sure the everyday practical use of this skill, but it was impressive either way.
Process: The defined, repeatable, and improvable steps you document and train on to perform a function.

Processes are so valuable they can be protected by a legal patent. Processes can drive the profitability and success of the business. They are often one of the key assets we review for when implementing an information security program.
Technology: Tools used to accomplish, speed up, or increase the impact of the security goals.

Like a builder who is responsible for framing a house, without a hammer it will take considerably longer and probably decrease the quality. The investment of tools allows greater speed, profit, efficiency and use of resources. Tools can sometimes even be measured by their ‘return on investment’.
Program Example
Let’s take a look at how these pillars impact a specific program like asset management.
In the story I shared above about the company with rooms full of boxes of security technology it would look like this:
Let’s start the example with the foundation of a thriving business that has a significant risk that justifies risk reduction. In addition, leadership supports that goal of reducing risk through an effective information and cybersecurity program. The security program leader has defined a goal of:
Asset Mangement – Know what compute assets we have within the company, and connected to the business so that we can apply appropriate security controls. Without knowing what we have, we cannot effectively reduce risk. Assets should be identified within a 97% accuracy and updated on a weekly basis so that reporting can be provided monthly.
People –
If you’re starting from scratch you can start to go to market looking for someone with the skills to help. The default approach is to look for someone with a resume that matches the keywords for ‘asset management‘ and maybe has a security certification to boot.

A better approach might be to estimate some initial numbers like; company size based on employees, locations, and assets. Go to your trusted social circles of other professionals, networking meetings, or consultants and ask them to compile a list of questions that will help search for and assess potential candidates. The golden nuggets you’re looking for are questions that will separate the wheat from the chaff. What can you ask that will show if the candidate has worked with a product (technology) that can do some asset management, versus a candidate that truly grasps and understand the critical functions and philosophies, and goals of a successful asset management program?
Questions might include:
- How do you find assets that we do not currently know about?
- How will you identify assets that are mobile, like laptops that might not be on during scheduled scan times?
- What tools do you like to use? What are the shortfalls, or weaknesses of those products?
- What are some techniques you use to identify assets that others are not using?
- What will you require from us (as an existing program ) to execute a successful program?
- If you could only use open-source or freeware, could you still perform an asset management function?
- How do you handle discrepancies in asset reporting? Like an asset was there but isn’t now, or an asset is there now but wasn’t before, or an asset shows up at a different location or two assets with the same name?
Process –
The cybersecurity profession is one of collaboration. It’s one of the few industries that do not see other competing business as competition, but instead as teammates. We’re truly fighting a battle. We want all the help we can get to stop the bad buys from stealing the sauce. If you’re in the same industry, that means you’ll have a huge advantage collaborating on what you’re seeing and what you’re doing about.
The cybersecurity industry has developed and continues to mature, a process for just about every security discipline and security program you can imagine. Most are universal, but some are vertical-specific, and business size specific.
Quick Pitch – Security process improvement is at the core of what we’re focused on at Asher Security. With decades of experience across multiple industries, we’ve compiled a list of macro and micro-processes that can be implemented to get traction and progress. We’ve refactored leading processes that the big companies use and make it practical and cost-effective for medium and small businesses to implement and take advantage of. These process improvements act as force multipliers. They are inexpensive to implement (most are free) and recover resource spend. Freeing you up, and allowing your team to focus on what’s most important.
Questions might include:
- What is the best way to dynamically identify business risk as an on-going process?
- What methodology can we use to identify assets and assign ownership?
- What is the process when a new unidentified asset appears on the network?
- What is our source of truth for network ownership that can be leveraged for scanning for assets?
- What process do we follow when there is justification to scan a network not listed in the source of truth?
- What expectations can we give legal to include in all partner agreements so that we can identify our assets, or our data, traversing partner networks?
- How long should we retain asset information after is no longer active?
- What process can we document and assign to IT for notifying security of new assets?
- Is there an approval, or sign off process, like collecting and validating change records for new assets identified?
- What is the escalation and approval process for security to quarantine, remove, or unplug an asset on the network?
Technology
What’s the best tool for the job? Is it the software or SaaS solution listed in the upper right of the Gartner Magic Quadrant? Should it be open-source or vendor-specific?

Going back to what supports these ‘resource pillars‘, we see culture, leadership, philosophy, and vision. As an analyst or security engineer, I have found it extremely helpful when security leadership creates tenants for the program. These tenants act as guide rails for technology decision making.
An example of a security tenant that a prior leader provided to me was, “We will invest in market-leading vendor solutions. They do not need to be ‘best-of-breed’. We will try to leverage a single vendor to accomplish as many security functions as practical and beneficial.”
This statement was short and simple. It gave me peace and greatly reduced the scope and breadth of vendor solutions I needed to consider and review. It said a lot in very few words.
I didn’t know it at the time, but this leaders philosophy has been a standard as I’ve engaged with businesses across diverse industries and sizes. The general rule I”ve seen is smaller companies with smaller information security programs and teams want big security vendors that can do it all. As the teams scale up, they start implementing other vendor solutions that are specific to the risks they are trying to reduce. These solutions require employee scaling as the skills needed go deeper. And as the companies get larger, they start to bring developers in house and can finally support open-source platforms and solutions.
When considering technology tools to help implement a security program you can ask these questions:
- Is there an asset management solution that can support our goal?
- Of those solutions do we want to support an open-source project, or spend more to get vendor support?
- Would any of the available solutions offer auxiliary benefits and help with the other security management initiatives?
- How hard do we believe it will be to acquire and sustain employees that can manage this solution?
- What technologies are my industry peers using to accomplish this goal?
- Which technology vendors are supporting education, networking events, security associations?
- If we don’t like this product in a year, how hard will it be to export our data and move to another solution?
- Are their departments outside information security that are going to be depending on the solution we choose for their own initiatives and requirements (compliance)?
Maturity Assessments
One thing I really like about a security maturity assessment, that is performed well, is that it drives into measuring these resource pillars. A good cybersecurity maturity assessment will bring to the surface the security opportunities, and highlight the best way to accomplish those benchmark goals through either people, process, or technology improvements.
If you’re unsure where you’re at as far as success benchmarks with your resource pillars, a security maturity assessment might be a great place to start.
Improving Resources
So if our security programs depend on these ‘resource pillars’, then the next question becomes how can we improve our pillars?
In the next article, we’ll examine some ways you can assess, plan, and invest in building up stronger security resource pillars.


Great article, Tony!