Are you concerned with moving your data to the cloud?
Are your partners and vendors starting to host your solution on SaaS or PaaS model and you want to develop your security review process?
Problem
I get it. I was in that position when I learned, only when I explicitly asked where our data was, that the vendor had moved to an external cloud solution. While I was trying to figure out the right questions to ask the vendor to ensure it was done securely, I was learning our internal application developers were starting to build applications hosted on a public cloud! I felt like my security program was falling out from underneath me. For the first time in a long time, I was unprepared and ill-equipped to address the risks facing the organization.
In an effort to build a security process I leveraged ‘value-add‘ vendors, only to be presented with a quote for a product they thought would help (but it didn’t even address the core issue).
Solution
There is more to a strong security program than just products. It should include people (knowledge), process, technology, and sometimes even a little security philosophy.

When we have a BIG issue, the best way to address it by breaking it down into smaller chunks. With cloud security that means unwrapping all the layers that make up this solution and reviewing them one at a time.
This security solution should start with the risk. And risk should be based on the data. Sometimes it can be based on the application due to availability, but most often it’s the sensitive and confidently data that needs to be protected.
By breaking down the security solution into layers we come up with a solid cyber strategy.
Layers
Data: What is the sensitivity?
If you want to build a solid cybersecurity strategy you should really consider ranking your data. Because the goal of a cybersecurity program is to protect the crown jewels (your data). It’s really helpful to identify what data that is and who can have access to it, and how and who it can be shared with.
Here’s a great article on building a data classification strategy
Application: What is the criticality of the applications?
It’s a great idea to have a list or database of your applications. If not all of them, at least the ones that are really important and you want to track.
We can rank application criticality based on risk mythology. That method will often include the sensitivity of the data the application transmits or processes, how important the availability of the application is, and if there are compliance requirements.
It’s easy to create a simple risk scoring guide. For example, give each of the following one point if true:
- Does it host sensitive or confidential data?
- Is it available externally?
- Does the business depend on its availability?
- Is the application in scope for compliance?
With a score of zero to four, you can quickly prioritize efforts around securing these systems.
Compute platform: Is the application being hosted on a stand-alone server, a virtual machine environment, or on containers?
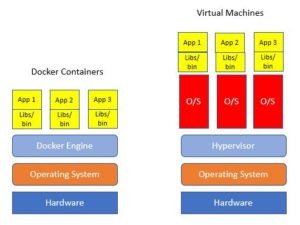
Based on this information, the individual vendor solutions (like ‘Docker’) can be defined and reviewed for specific security standards.
The methodology to secure an application running on Docker and Kubernetes in Google Cloud Platform is very different than securing and application running Windows virtual machine.
Cloud Platform: Private or Public cloud?
Again by asking the appropriate scoping questions, then more specifics can be drilled down into like the public cloud vendor (AWS vs. Azure vs. GCP).
Then security standards and checklists can be built for administrators to apply the specific security configurations that make up these best practices. Using the Center for Internet Security standards can be a great starting place.
Summary
This probably wasn’t the exact solution you were looking for, but this is where it needs to start. Now that you’ve taken a very BIG issue and broken it down into bite-size chunks we can start building the specific policies, security guides and standards, and security capabilities that make up the security program.
We can help.
We offer a lot of content to help equip you to move forward building your strategy. For example, if your solution is hosted on Docker, Kubernetse, and Google Cloud Platform we have a six-part series on how to secure it!

We also offer consulting services where we can come onsite, review what you’ve got going on and work with you to build out a custom cybersecurity strategy.
We also piloting a ‘Secure the Cloud’ workshop. The focus of this workshop is to walk through technology stack, starting from the data to the policy and then to all the technology layers and work to build a comprehensive security guide and checklist your company can leverage to ensure it’s being done securely and consistency. We’re currently still looking for a couple more pilot clients that will get this workshop at a deep discount. We want to make sure is the most powerful, valuable, and amazing cloud security workshop ever before we roll it out.
If you’re interested in being a pilot customer, and want to enjoy a deep discount but receive the full value (plus more), schedule a kick-off call below.
Asher Security is a Minnesota cybersecurity consulting group that helps businesses decrease risk and decrease expense by partnering to mature security programs.


Recent Comments